ImageTragick
Sprache: Englisch
GraphicsMagick Image Processing System graphicsmagick.org
GraphicsMagick is a robust collection of tools and libraries to read, write, and manipulate an image in any of the more popular image formats including GIF, JPEG, PNG, PDF, and WebP. With GraphicsMagick you can create GIFs dynamically making it suitable for Web applications. You can also resize, rotate, sharpen, color reduce, or add special effects to an image and save your completed work in the same or differing image format.
ImageMagick - Create, Edit, Compose, or Convert Digital Images imagemagick.org
Use ImageMagick® to create, edit, compose, and convert digital images. Resize an image, crop it, change its shades and colors, add captions, and more.
BleepingComputer | Cybersecurity, Technology News and Support bleepingcomputer.com
BleepingComputer is a premier destination for cybersecurity news for over 20 years, delivering breaking stories on the latest hacks, malware threats, and how to protect your devices.
jQuery Lightbox Generator. Mobile-ready, Responsive Lightbox Gallery visuallightbox.com
Create terrific lightbox jQuery slideshows in second without a line of code. All browsers and devices!
Schnelles & klimapositives WordPress Hosting - 50% Rabatt raidboxes.io
WordPress Hosting ✓ schnell ✓ sicher ✓ klimapositiv. Mit persönlichem Support und kostenlosem Umzug. Über 16.000 Kunden vertrauen uns. Jetzt loslegen!
enigma0x3 | Red Teamer and Security Addict enigma0x3.net
Red Teamer and Security Addict
4shared.com - Kostenloser Dateiaustausch und -speicher 4shared.com
Online file sharing and storage - 15 GB free web space. Easy registration. File upload progressor. Multiple file transfer. Fast download.
Welcome to nginx! osvdb.org
DeepEnd Research deependresearch.org
CVE security vulnerability database. Security vulnerabilities, exploits, references and more cvedetails.com
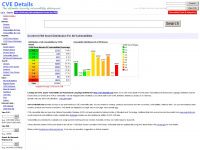
CVEDetails.com is a vulnerability intelligence solution providing CVE security vulnerability database, exploits, advisories, product and CVE risk scores, attack surface intelligence, open source vulnerabilities, code changes, vulnerabilities affecting your attack surface and software inventory/tech stack. You can view CVE vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and vulnerability trends over time
Iso Warez isowarez.de
FragAttacks: Security flaws in all Wi-Fi devices fragattacks.com
We present three security design flaws in Wi-Fi and widepread implementation flaws. These can be abused to exfiltrate user data and attack local devices.
Buy Plugins & Code from CodeCanyon codecanyon.net
Discover 32, 656 Plugins, Code and Script for Bootstrap, Javascript, PHP, Wordpress, HTML5 and more. Save time, buy Code on CodeCanyon!
Blog Noteshexe | Blog Anett Hammerschmidt noteshexe.de
Blog Anett Hammerschmidt
VULNERABILITY LAB - SECURITY VULNERABILITY RESEARCH LABORATORY - Best Independent Bug Bounty Programs, Responsible Disclosure & Vulnerability Coordination Platform - INDEX vulnerability-lab.com
VULNERABILITY LAB - SECURITY VULNERABILITY RESEARCH LABORATORY - Best Independent Bug Bounty Programs, Responsible Disclosure & Vulnerability Coordination Platform
Infinity Forensics - Computer Forensics Singapore, Mobile Recovery Investigation & Ediscovery infinityforensics.com
Infinity Forensics Singapore offers computer forensics & digital crime investigation & Mobile recovery for litigation and digital private investigation
28 Online Vulnerability Scanners & Network Tools | HackerTarget.com hackertarget.com
Online Vulnerability Scanners to map the attack surface and identify vulnerabilities. 28 trusted open source security scanners and network tools.
morph3us.org morph3us.org
HTTPCS by Ziwit | Cyber Security tools and services for your Business httpcs.com
Detect security flaws on your site, analyze your response times, anticipate cyber attacks, and check your content's reliability. Online tools and audit services to secure and protect your site against cyber risks, hacking and data theft.
geosystemics.com geosystemics.com
Exploit Shop | 1-day vulnerability analysis using DarunGrim exploitshop.wordpress.com
1-day vulnerability analysis using DarunGrim
Malware Intelligence Blog. A division of MalwareIntelligence malwareint.blogspot.com
Packet Storm packetstormsecurity.com
Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers
firstandonly.de firstandonly.de
Neal Poole nealpoole.com
My name is Neal Poole. I'm interested in web application security.
Exploit Database - Exploits for Penetration Testers, Researchers, and Ethical Hackers exploit-db.com
The Exploit Database - Exploits, Shellcode, 0days, Remote Exploits, Local Exploits, Web Apps, Vulnerability Reports, Security Articles, Tutorials and more.
Wir arbeiten an einer neuen Site für Sie computergmbh.de
Digital Defense | The Vulnerability Management Solution digitaldefense.com
Digital Defense's Frontline Vulnerability Management program is the highest level of accuracy and performance in a layered security solution.
What is it? - NoScript: block scripts and own your browser! noscript.net
The NoScript Security Suite is a free extensions for Firefox, Chrome and other browsers, preemptively blocks malicious scripts and allows JavaScript and other potentially dangerous content only from sites you trust. Download it now for free!
SecLists.Org Security Mailing List Archive seclists.org
Security mailing list archive for the Nmap lists, Bugtraq, Full Disclosure, Security Basics, Pen-test, and dozens more. Search capabilities and RSS feeds with smart excerpts are available
MacOS Container-like Virtualization for DevOps and iOS CI/CD - Veertu veertu.com
Optimize your iOS CI/CD using Anka's macOS container-like Virtualization. Store VM state in the Anka Registry and run on any Apple hardware.
Brakeman brakemanscanner.org
Brakeman is a static analysis security vulnerability scanner for Ruby on Rails applications.
KRACK Attacks: Breaking WPA2 krackattacks.com
This website presents the Key Reinstallation Attack (KRACK). It breaks the WPA2 protocol by forcing nonce reuse in encryption algorithms used by Wi-Fi.
HackerOne | #1 Trusted Security Platform and Hacker Program hackerone.com
Reduce the risk of a security incident by working with the world's largest community of trusted ethical hackers. HackerOne offers bug bounty, VDP, security assessments, attack surface management, and pentest solutions.
Nibble Security nibblesec.org
NibbleSecurity Blog
Code Security | Kiuwan kiuwan.com
Cloud based code security for your DevSecOps process. Kiuwan provides end to end application security with SAST, SCA and QA to help your team find and fix vulnerabilities fast.
bavotasan.com - Home of c.bavota, web developer extraordinaire and creator of multiple WordPress themes and plugins bavotasan.com
Home of c.bavota, web developer extraordinaire and creator of multiple WordPress themes and plugins
cl3mentino | Gib Windows keine Chance! Unix 4 ever! cl3mentino.wordpress.com
Gib Windows keine Chance! Unix 4 ever!
PHP 8.1.22-he.0 - phpinfo() berlin-kult-tour.de
CODE WHITE | Blog codewhitesec.blogspot.com
Secplicity - Security Simplified secplicity.org
Secplicity provides daily video and editorial content about IT security for today's busy professional. Real news, real solutions, real simple.
TrustedSite Certification | Build trust and boost sales. trustedsite.com
Almost Secure palant.info
Wladimir Palant's blog
ImmuniWeb® AI Platform | Penetration Testing, Dark Web Monitoring, Attack Surface Management and More immuniweb.com
ImmuniWeb® AI Platform for Application Security Testing, Attack Surface Management & Dark Web Monitoring. Try now.
httpoxy httpoxy.org
httpoxy is a vulnerability in PHP and CGI web applications that allows remote attackers to proxy requests
SecurityBridgeTM // Threat Intelligence for SAP security 2024 securitybridge.com
Threat Intelligence for ultimate SAP security by anomaly detection. A holistic security platform, covering all vital aspects to protect SAP.
Live Patching for Linux Kernels - KernelCare Enterprise - TuxCare tuxcare.com
Experience Seamless System Maintenance with TuxCare's Live Patching Solutions and Extended Lifecycle Support
External Threat Landscape Management | Attack surface | Brand | Vulnerability | Cyber Threat Intelligence cyfirma.com
A leading external threat landscape management company transforming cyber threat intelligence by giving attack surface, brand, Vulnerability intelligence along with digital risk monitoring, situational awareness, and third-party risk in a unified view.
Complete External Attack Surface Management | Detectify detectify.com
Use Detectify to get complete coverage of your growing attack surface with Surface Monitoring and Application Scanning.

 zu imagetragick.com
zu imagetragick.com